Hey there! If you’re looking to beef up the security of your VMware ESXi hosts, you’re in the right place. We’re going to walk through some key strategies that are not just effective but also straightforward to implement. No unnecessary jargon, just straight-up useful info.
Introduction to VMware ESXi Security
First off, let’s get a lay of the land. VMware ESXi is a big deal in the virtualization space, and rightly so. But, like anything valuable, it attracts attention – not all of it good. That’s why securing your ESXi environment is crucial. We’re talking about protecting your virtual environments from those pesky threats that lurk around the digital corner.
Understanding VMware ESXi Vulnerabilities
So, what’s at risk? Well, VMware ESXi hosts can be vulnerable to various security threats – from malware and viruses to unauthorized access. Knowing what these vulnerabilities are is half the battle. We’ll explore the most common threats and how they can potentially wreak havoc on your system.
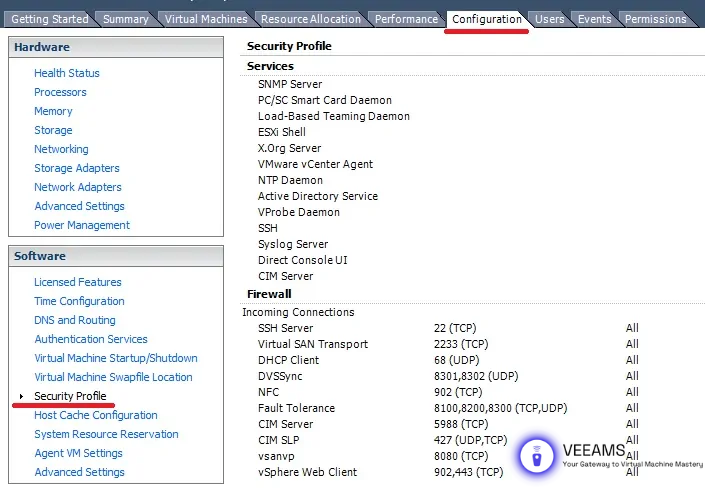
Configuring ESXi Firewall Settings
Configuring the firewall settings on your ESXi hosts is like setting up a robust fence around your digital property. It’s all about keeping the bad guys out while allowing legitimate traffic to pass through. So, how do you do this effectively?
First, access the ESXi host using the vSphere Client. Once in, navigate to the ‘Configuration’ tab and select ‘Security Profile’. Here, you’ll find the firewall settings. You can manage inbound and outbound rules based on service names, port numbers, and IP addresses.

For example, if you have a service that should only be accessible internally, limit its access to internal IP ranges. Also, regularly review these rules to ensure they align with your current operational needs. Remember, a firewall that’s too lax is almost as bad as having no firewall at all.
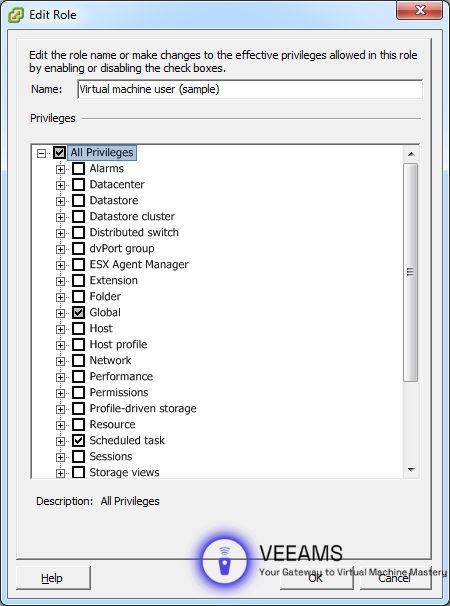
Managing User Access and Permissions
When it comes to user access, think ‘need-to-know basis’. Not everyone requires full access to your ESXi environment. Managing user access efficiently can significantly reduce the risk of internal threats and accidents.
Start by creating roles with specific permissions in vCenter Server. Assign these roles based on the principle of least privilege – users should have just enough permissions to do their job and no more. For instance, a junior admin might not need access to datastore management.

Regularly audit user access levels and adjust as necessary. This is especially important when employees change roles or leave the organization. Tight control over who can do what on your ESXi hosts is a cornerstone of a secure environment.
Implementing Network Security Measures
Your network is the highway all your data travels on. Securing this highway is critical to protect the data and ensure that only authorized traffic can flow in and out of your VMware ESXi hosts.
Begin by isolating your network traffic. Use VLANs to segment network traffic into different categories – management, vMotion, storage, etc. This not only improves performance but also limits the scope of any potential security breach.
Implement strong encryption for data-in-transit. Technologies like SSL/TLS should be used for securing console connections and other sensitive communications. Additionally, consider using VPNs for remote access to ensure that data is encrypted even when accessing your system from outside the network.
Network security policies should also be regularly updated and audited. Just like a city changes its traffic rules to improve safety and efficiency, your network policies should evolve to meet new challenges and threats.
Regular Updates and Patch Management
Keeping your VMware ESXi hosts updated isn’t just about getting the latest features; it’s a critical security practice. Each update or patch can potentially fix security vulnerabilities, making your system more secure.
Set a regular schedule for checking and applying updates. VMware often releases patches that address specific security vulnerabilities. It’s crucial to apply these patches promptly to protect your hosts from known exploits. You can manage updates manually through the vSphere Client or automate them using vSphere Update Manager for a more streamlined process.
Remember, before applying any updates, it’s wise to back up your configurations and test the updates in a non-production environment. This way, you ensure that the updates won’t negatively impact your system.
Monitoring and Auditing for Continuous Security
Continuous monitoring and auditing are like having a vigilant security guard on duty 24/7. It’s essential for early detection of any unusual activity that could indicate a security breach.
Utilize tools like VMware vRealize Log Insight or third-party solutions for continuous monitoring. These tools can help you track real-time events and logs, giving you insight into what’s happening on your ESXi hosts. Set up alerts for suspicious activities, like multiple failed login attempts or changes in configuration settings.
Regular auditing is also crucial. Review logs and settings periodically to ensure everything is as it should be. Audits can help you spot potential vulnerabilities before they’re exploited and ensure compliance with security policies.
Conclusion and Best Practices Recap
In conclusion, securing your VMware ESXi hosts requires a combination of proper configuration, vigilant monitoring, and regular maintenance. By following the practices outlined in this guide, you can significantly enhance the security of your virtual environment.
Let’s quickly recap the best practices:
- Configure firewall settings effectively to control traffic.
- Manage user access and permissions judiciously.
- Implement network security measures, including VLANs and encryption.
- Stay on top of updates and patches to protect against vulnerabilities.
- Monitor and audit your system regularly to detect and prevent security issues.
Securing your VMware ESXi hosts is an ongoing process, but with these strategies in hand, you’re well on your way to creating a robust and secure virtual environment.
